Anatomy of a Phishing Attack
Anatomy of a Phishing Attack
Chuck Davis, MSIA, CISSP-ISSAP
Abstract
Phishing is the use of social engineering to obtain personal information for the purposes of identity theft. Phishing typically comes in the form of an email, disguised to look as if it was sent by a trusted source, and requesting personal information or authentication credentials.
As the tools to detect phishing become more effective, the phishing attacks themselves are becoming increasingly advanced and more difficult to identify.
This paper will show how a recent phishing attack from October 31, 2012, is representative of the type of attack that is not detected by spam filters and is likely to trick many recipients.
What is Phishing?
The United States Computer Emergency Readiness Team (US-CERT) defines phishing as follows.
Phishing is an attempt by an individual or group to solicit personal information from unsuspecting users by employing social engineering techniques. Phishing emails are crafted to appear as if they have been sent from a legitimate organization or known individual. These emails often attempt to entice users to click on a link that will take the user to a fraudulent website that appears legitimate. The user then may be asked to provide personal information such as account usernames and passwords that can further expose them to future compromises. Additionally, these fraudulent websites may contain malicious code. (http://www.us-cert.gov/nav/report_phishing.html)
Social Engineering, in the context of security, is understood to mean the art of manipulating people into performing actions or divulging confidential information.
The e-mail…
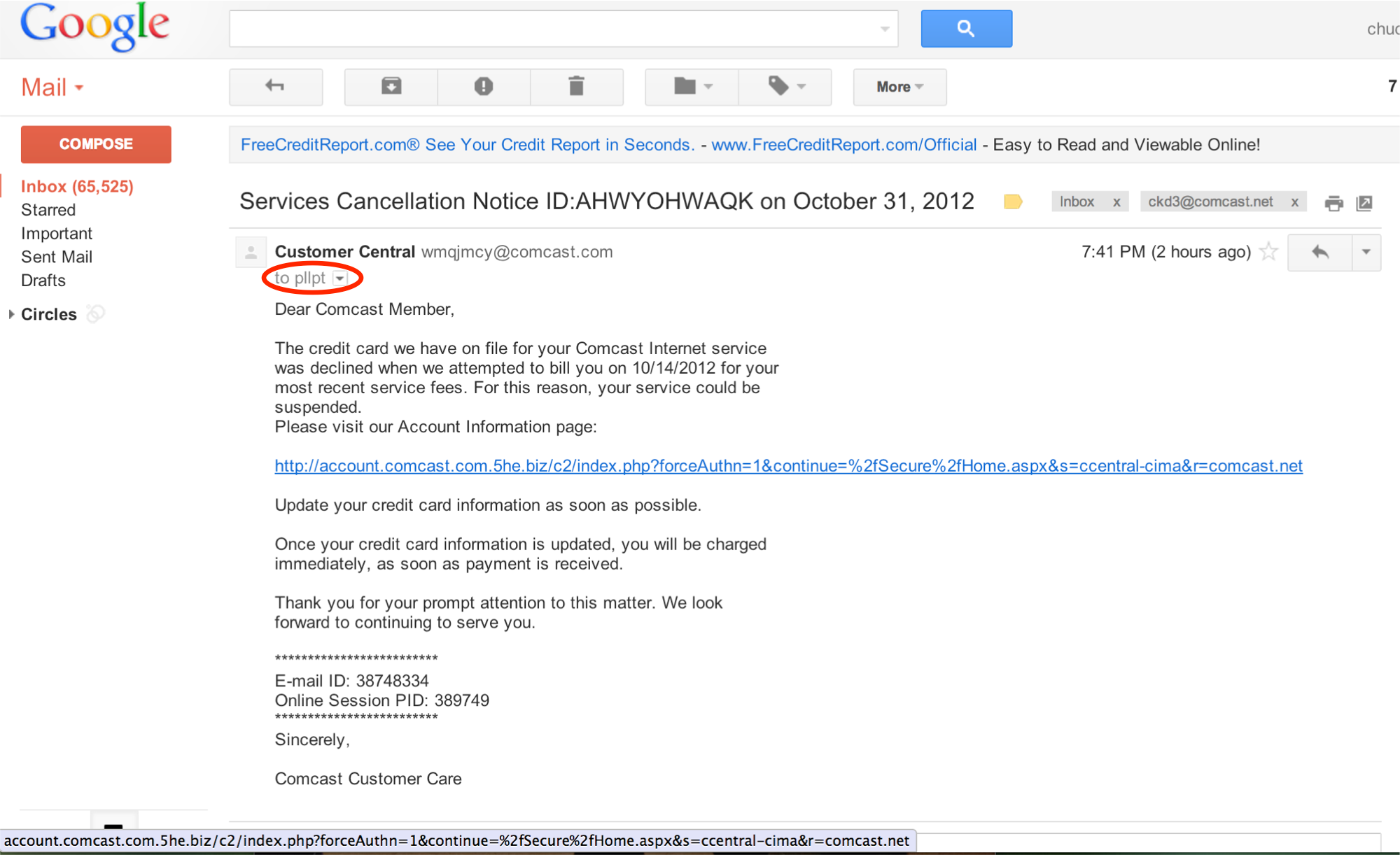
The following email appears to come from “Customer Central” from an e-mail address using the domain name, “comcast.com”.
Google does not do us any favors by masking the full destination email address. You can see in the image below that it appears to be sent to “pllpt”. This is greyed out and in small text.
The email indicates that the customer’s credit card information on file is declining the payment and the email requests that the recipient update his or her credit card information by clicking on the link.
A quick or casual review of this link may seem safe. The URL begins with, http://account.comcast.com
But look at the rest of the URL.
http://account.comcast.com.5he.biz/
Remember that the last two sections before the forward slash(/) indicate the domain name of the destination. In this case, the domain name is 5he.biz and account.comcast.com are all subdomains of 5he.biz.
Interestingly, the author of this Phishing email did not try to mask the actual link, which is easy to do and might be a little more effective in tricking someone to click on the link.
Clicking the link…
After clicking the link, you can see below that the URL has changed to yet another domain name. This time it begins with “login.comcast.net” but again, notice the trailing forward slash does not come until much later in the URL which means that the domain name for this page is actually o7b.name.
The next, very interesting thing to note here is that the rogue site looks very much like the actual Comcast xfinity authentication page. Below, compare the screenshots of the rogue site and the actual Comcast xfinity page. They are nearly identical!
The rogue site…
The real site…
Identifying a Phishing attack is becoming increasingly more difficult. To reduce the likelihood of becoming a victim, follow the tips below.
Don’t click on links in email. If you get and email from a seemingly trusted source, like your bank, open your web browser and log in using a bookmark or a known, trusted address.
Don’t click on short URL’s. Short URL’s are very popular with Twitter and other social media. If you encounter a short URL, verify the destination with a tool or website that will reveal the destination address, like checkshorturl.com.
If you must click on a link, verify the URL beforehand. Rather than click on the link, hover your mouse pointer of the link and right click and choose the option to copy the destination address. Then paste it in your browser so you can review it. If the address looks suspicious, don’t hit enter and delete it from your browser.
Report it! If you feel you have received a phishing email, forward it to the United States Computer emergency Readiness Team (US-CERT) at the following address: [email protected].
Summary
Early phishing attempts were very simple and easy to spot. Today, phishing is becoming much more advanced. As security tools become more efficient at identifying attacks, the attacks become more difficult to identify. This certainly holds true for phishing; as we see these attacks becoming more advanced we need better tools and more end user awareness to protect ourselves and our identities.