BTH News 04July2020
This Week In Cybersecurity
This week on Between the Hacks, July 4th Edition, voting vulnerabilities, Roblox hacked to promote Trump, a new bill that threatens encryption and free speech, the NSA shares VPN security strategies, and a book (and upcoming documentary) that reveals details of global cyber tension.
Voting Vulnerabilities
2020 has been a challenging year to say the least and we’re only half-way through it. While we don’t know what the back end of this year will bring, we do know that the U.S. will have an election and there is a lot of talk about flaws in the voting system. In March, Between The Hacks reported on HBO's 2020 documentary, Kill Chain that reveals how many of the U.S. voting machines are vulnerable to attack.
Nation-state interference is again, a real concern because not only is the voting technology vulnerable, but social media has given opposing nation-states a medium with which to spread false information to misinform voters. “Leading up to the United States 2018 midterm elections, Radware surveyed Facebook users on the safety of U.S. elections and the results reveal a pessimistic situation. The overwhelming majority (93.4 percent) of respondents believe that the United States election system is vulnerable to targeting and hacking” reports Security Boulevard.
Voting machines and mail-in ballots aren’t the only concern. Yahoo! reports that the real problem lies with voter registration. Famed hacker, Jack Cable found, “massive vulnerabilities in the Illinois voter registration system that could have allowed hackers to see and potentially alter voter data.”
There is no perfect voting solution, however many technology experts recommend that until a better solution is put in place, the U.S. use paper ballots which are the most reliable, resilient to fraud, and paper ballots provide a means to validate and recount if necessary.
Image from BleepingComputer.com
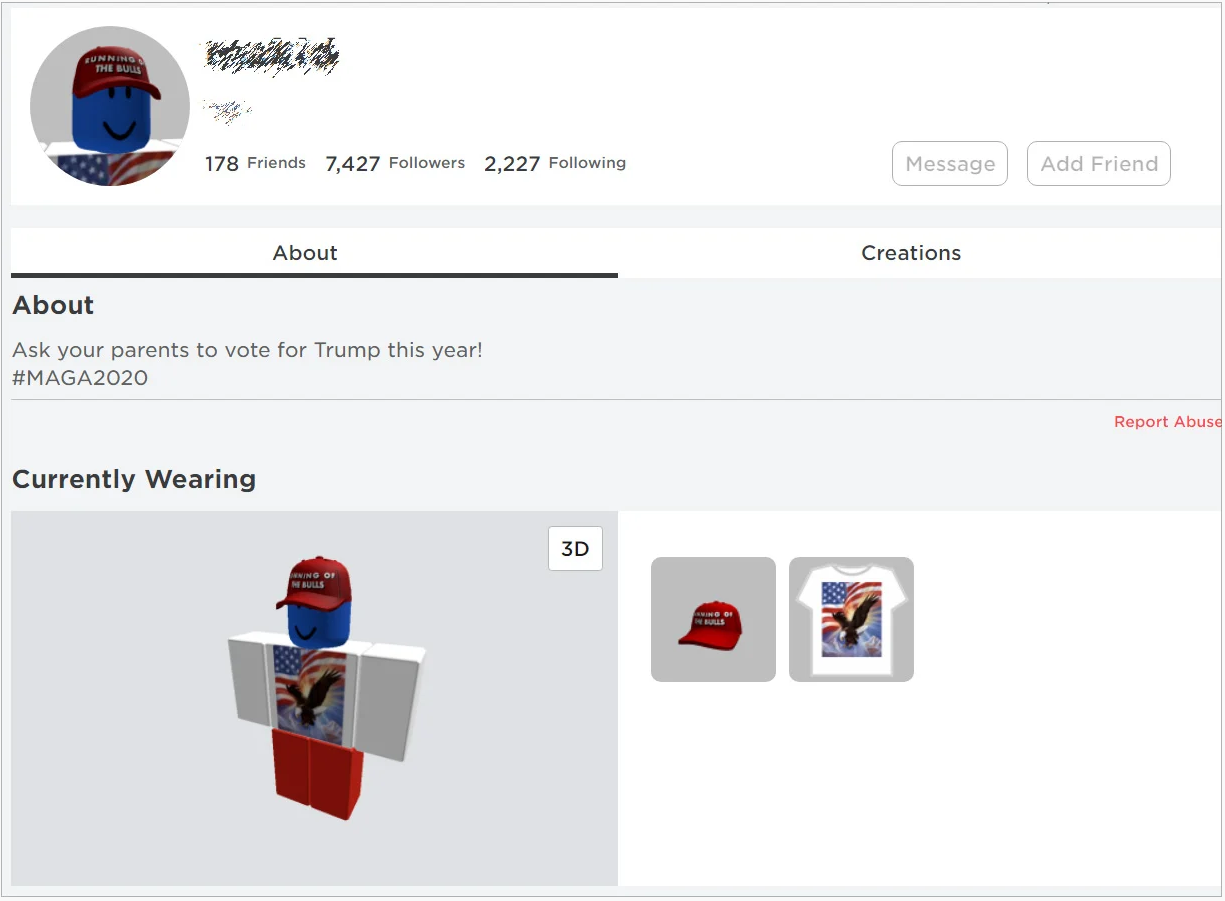
Roblox accounts hacked in support of Trump re-election
Roblox, the online gaming and social platform has over 100 million active monthly users. The platform has users of all ages but many are between the ages of 9 and 14 years old. In addition to gaming, Roblox users can create an avatar and buy “skins” to customize the appearance of their avatar.
According to a July 3rd update to Bleeping Computer's coverage of the story, hackers have compromised over 2000 Roblox accounts. “Targeted at children, once the hacker gains access to each account, they modify the About section of the profile to read, ‘Ask your parents to vote for Trump this year! #MAGA2020.’" The attackers have also changed the victim’s avatars to wear hats and shirts that look like standard attire for a Trump supporter.
Graham Cluley recommends that affected Roblox users would be wise to change their passwords to something unique to their Roblox account and they should also enable two-step verification (2SV) on Roblox for a higher level of security.
Image from eff.org
New Bill Threatens Encryption and Free Speech
The EARN IT Act was introduced by U.S. senators in early March. This bill has been highly controversial because it, “could be used to drastically undermine encryption. Although the bill doesn’t use the word ‘encryption’ in its text, it gives government officials like Attorney General William Barr the power to compel online service providers to break encryption or be exposed to potentially crushing legal liability” according to the Electronic Frontier Foundation (EFF).
The debate around government-managed encryption back doors has been happening for years. U.S. law enforcement and politicians have stated that they need this power to stop child predators and terrorists. The tech companies, who actually understand encryption and technology, make the counter argument that encryption is math and strong encryption already exists and is free for anyone to use. So, if you make strong encryption illegal, then only the criminals will use it which doesn’t solve the problem that the politicians are claiming to try and solve. The EFF claims that the EARN IT Act is unconstitutional in many ways, including violations of first and fourth amendment rights. If the government is trying to get the ability to read everyone’s digital communications, where does that end? Will they next be installing cameras and microphones in our homes and cars so they can listen to our personal conversations and claim that it is to protect us from child predators and terrorists?
You can learn more on the EFF’s website. Two additional articles are listed below.
The New EARN IT Bill Still Threatens Encryption and Free Speech July 2, 2020
Tell Your Senator: Vote No on the EARN IT Act June 30, 2020
NSA releases guidance on securing Virtual Private Networks
With most people are working from home due to COVID-19, many companies and organizations are using virtual private networks (VPN) for the first time in order to allow employees to securely access their organization’s internal data resources.
In an effort to assist these organizations with securing their VPN solutions. the U.S. National Security Agency (NSA), “has published guidance on how to properly secure IP Security (IPsec) Virtual Private Networks (VPNs) against potential attacks” reports Bleeping Computer.
These recommendations come after a number of vulnerabilities have been disclosed in popular VPN technology in recent months.
Tip of the Week
The Perfect Weapon: A Book Turned Documentary
Do you want to understand which countries have formed an active cyber-offensive and what their motivations are in cyberspace? If so, I recommend that you read, The Perfect Weapon: War, Sabotage and Fear in the Cyber Age.
This book, written by New York Times senior writer and national security correspondent David Sanger, shares first-hand accounts of Sanger’s interactions with heads of state, tech companies and influencers.
The Perfect Weapon is the startling inside story of how the rise of cyberweapons transformed geopolitics like nothing since the invention of the atomic bomb. Cheap to acquire, easy to deny, and usable for a variety of malicious purposes, cyber is now the weapon of choice for democracies, dictators, and terrorists. Two presidents—Bush and Obama—drew first blood with Operation Olympic Games, which used malicious code to blow up Iran’s nuclear centrifuges, and yet America proved remarkably unprepared when its own weapons were stolen from its arsenal and, during President Trump’s first year, turned back on the United States and its allies.
For those of you who have already read and enjoyed the book, you can now look forward to the HBO Documentary that is based on the book which is scheduled for a late 2020 release.