Phishing
Phishing is the attacker’s dependable, longtime friend. Around since at least 1995, phishing is used to trick people into providing credit card information, login IDs and passwords, and to gain access to your computer, protected systems and/or networks.
Phishing takes many forms and those forms evolve daily. It’s true, some phishing attacks are so good they can even dupe seasoned cybersecurity experts, but Between The Hacks readers should not be discouraged. On the contrary, common phishing attacks are easy to detect. And, the more you understand about phishing tactics, the better you get at recognizing when you need to be suspicious and take extra caution.
Today, Between The Hacks arms you with the following: phishing background, practical advice, realistic visual examples, and links to reliable resources. Much of this content comes from previous Between The Hacks posts, but this page is a single source for all of that content and will be updated with new content in the future.
As always, BTH is interested in your feedback, questions and insight. Contact us with your thoughts or suggestions. Between The Hacks will continue to update content on this page, as the topic of phishing is a constantly evolving topic.
Topics
WHAT IS PHISHING?
Phishing is the malicious use of social engineering to obtain sensitive information or access from an unsuspecting victim. This usually comes in the form of email, social media links, or other digital means that an attacker can use to trick a victim.
The United States Computer Emergency Readiness Team (US-CERT) defines phishing as follows.
Phishing is an attempt by an individual or group to solicit personal information from unsuspecting users by employing social engineering techniques. Phishing email is usually crafted to appear as if they have been sent from a legitimate organization or someone known to the recipient. They often attempt to entice users to click on a link that will take the user to a fraudulent website that appears legitimate. The user then may be asked to provide personal information such as account usernames and passwords that can further expose the victim to future compromises. Additionally, these fraudulent websites may contain malicious code. (http://www.us-cert.gov/nav/report_phishing.html)
History of Phishing
The practice of phishing, “originated sometime around the year 1995, these types of scams were not commonly known by everyday people until nearly ten years later” according to phishing.org. The practice has become one of the main methods of attack and is increasing at a rapid pace.
Understanding the history of phishing can help you avoid falling prey to this type of scam. To learn more about the history of phishing, read this post on phishing.org.
Basic Phishing
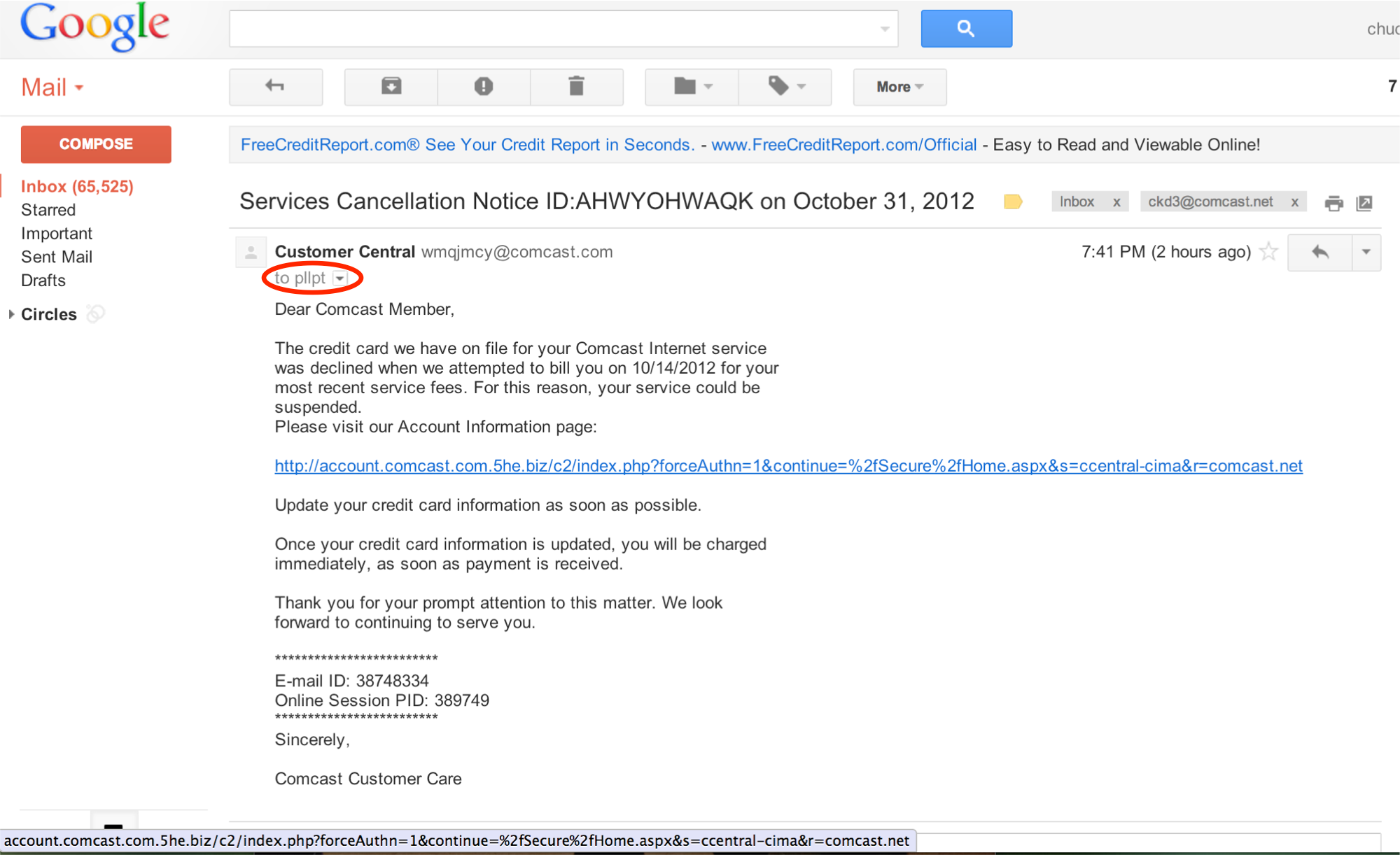
Phishing attacks come in all shapes and sizes. Most of the basic phishing email have easy to spot characteristics, if you’re looking for them. The following example is from 2012. Even though it’s old, I think this email would still trick many recipients.
You can see in the following image, that the email appears to come from “Customer Central” and sent from an e-mail address using the domain name, “comcast.com”.
Gmail does not do us any favors by masking the full destination email address. You can see in the image below that it appears to be sent to “pllpt”. This is greyed out and in small text so it’s easy to overlook but the fact that the recipients real email address is not in the “To:” field, is our first clue that this may be a phish.
The email indicates that the customer’s credit card information on file is declining the payment and the email requests that the recipient update his or her credit card information by clicking on the link.
A quick or casual review of this link may seem safe. The URL begins with, http://account.comcast.com
But look at the rest of the URL.
http://account.comcast.com.5he.biz/
Remember that the last two sections before the forward slash(/) indicate the domain name of the destination. In this case, the domain name is 5he.biz and account.comcast.com are all subdomains of 5he.biz.
Interestingly, the author of this Phishing email did not try to mask the actual link, which is easy to do and might be a little more effective in tricking someone to click on the link.
CLICKING THE LINK…
After clicking the link, you can see below that the URL has changed to yet another domain name. This time it begins with “login.comcast.net” but again, notice the trailing forward slash does not come until much later in the URL which means that the domain name for this page is actually o7b.name.
The next, very interesting thing to note here is that the rogue site looks exactly like the actual Comcast xfinity authentication page. Below, compare the screenshots of the rogue site and the actual Comcast xfinity page. They are nearly identical!
The rogue site…
The real site…
In March of 2017, Google stated that its machine learning models now can detect and stop spam and phishing with 99.9% accuracy. However, this is a cat and mouse game that has been played for years by the spammers/phishers on one side and the spam filter developers on the other side. Once the defenses get better against the latest spam attack methods, the spammers change their tactics to bypass the filters.
Below is an example of a fairly obvious spam email that Google’s filter caught and put in the Spam folder of my Gmail account. There is no subject, it just includes a link. When Google discovers rogue links, the message in the red box shown in the email serves as a warning not to click on links or reply with personal information.
Advanced Phishing Tactics
Many of you reading this have received phishing email and you likely know some tricks to identify a basic phish. In this section, you may learn some new tactics that attackers are using to trick us.
Tactic #1: URL Masking
This tactic is actually quite basic but it is the cornerstone of more advanced tactics. One of the main tips in finding a phishing email, is to hover over links to see where they go before you click. That is a great tip but there are phishing tricks that attackers use to mask a URL. Here are some examples of how easy it is to mask a URL. If you hover over the link below, you’ll notice that it does not link to yahoo.com, but rather, google.com.
Tactic #2: Advanced URL Masking
Hovering over is a good way to scrutinize a url but it’s not 100%. There are ways to “click-jack" urls that will show one link when you hover over it but send the user to another link when you click.
One method of executing this is to write JavaScript that shows one domain when you hover over the link, and sends you to a different page when you actually click! Hover over the following example. You’ll see that the link points to https:www.google.com. Now click on that link and see which page opens up.
Tactic #3: Unicode Domains
Another tactic is to use character sets that look similar to English/Latin characters, but are not. In this example, apple.com was registered using Cyrillic characters instead of English/Latin characters.
https://apple.com/ - This is the REAL Apple url with English/Latin characters
https://аррӏе.com/ - This is a fake site using Cyrillic characters
When you click on the second link in Firefox and some other browsers, the url shows the Cyrillic characters. The good news is that most modern browsers now show the Punycode url.
A security researcher registered the above domain. You can read his blog post here to learn more about this type of attack.
Tricking the Cybersecurity Defense Tools
As mentioned earlier, the world of cybersecurity is a constant cat and mouse game where attackers find new and creative ways to attack and the defenders discover those methods and figure out how to stop the attacks. The latest wrinkle in this spin around the hamster wheel was revealed by researchers at Barracuda Networks in April of 2020, who discovered that threat actors are now using, “reCAPTCHA walls to block URL scanning services from accessing the content of phishing pages.”
What this means is that if you are tricked into clicking on a link or opening an attachment from a phishing email, you might be met with a real, reCAPTCHA challenge which has you click a check box to prove that you are not a robot. In this context, a “robot” or a “bot” is an automated program that scours the Internet looking to scrape data from sites, create fake accounts or post fake reviews. When you click that box and pass the reCAPTCHA test, you are sent to the malicious phishing page. While clicking that box is an easy test for humans, the automated cybersecurity tools that check the links in our email work much like the malicious bots and are unable to get past that reCAPTCHA to determine if the page has suspicious or malicious content.
What is a CAPTCHA/reCAPTCHA?
CAPTCHA is an acronym that stands for, Completely Automated Public Turing test to tell Computers and Humans Apart. In 2009, Google acquired a popular version of CAPTCHA technology called the reCAPTCHA. Early versions of reCAPTCHA had website visitors trying to read distorted words, then type them in a box to prove that they are not a robot.
A later version of reCAPTCHA displays an image with grid lines and challenges visitors to solve a simple puzzle like, “Select all squares with traffic lights.” These reCAPTCHA methods are effective but frustrating to end users who sometimes fail the tests once or twice before success.
Google’s reCAPTCHA version 3 was created to relieve the end user of the stress and time needed to pass the previous reCAPTCHAs. In version 3, the visitor only needs to check a box to verify that he or she is not a robot. However, the results are similar in that automated bots, both good and bad, are unable to pass the test as see the page behind the CAPTCHA.
The Phish
In the past we have seen phishing pages mimic a reCAPTCHA to make a site look more credible, but now that tactic seems to have been replaced by attackers actually using a reCAPTCHA in most cases. According to Barracuda’s report, “only one email with a fake reCAPTCHA box was detected, compared to more than 100,000 emails using the real API.”
An example from the report shows a phishing page that appears to be an email from Microsoft that is alerting the recipient of a new voicemail. The email contains an attached html file that, when opened, redirects the victim to a reCAPTCHA page.
After the victim solves the reCAPTCHA, they are redirected to the actual phishing page which appears to be a standard Microsoft login page.
At this point, if the victim falls for the phish, the threat actors now have the victim’s Microsoft username and password.
The use of a real reCAPTCHA is a clever trick to make the victim feel as if the email is valid but it doesn’t just add credibility, it also keeps the automated security, spam and phishing tools from seeing the actual phishing page. Humans are the last line of defense so it’s important to stay alert when checking email because it is one of the few ways that threat actors have to get into our home and work networks.
Business Email Compromise (BEC)
Business Email Compromise (BEC) is a form of phishing attack that attempts to trick victims into sending money to the attacker. This attack is simple to execute and can be very costly to the victim. According to a 2018 FBI report, BEC attacks have earned scammers over 12 billion dollars. BEC is a type of phishing attack with the goal of tricking the victim into sending money to the attacker.
FIVE TYPES OF BEC
Phishprotection.com reports that there are five types of BEC.
Bogus Invoice Scheme When a business, which has a long standing relationship with a supplier, is requested to wire funds for invoice payment to an alternate, fraudulent account.
CEO fraud When the compromised email account of a high level executive is used to request a wire transfer to a fraudulent account.
Account compromise When an employee of a company has their email account compromised and it’s then used to request repayment of an invoice by a customer to a fraudulent account.
Attorney impersonation When victims are contacted by fraudsters identifying themselves as lawyers and are pressured into transferring funds to a fraudulent account.
Data theft When fraudulent e-mails are used to request either wage or tax statement (W-2) forms or a company list of personally identifiable information (PII).
With each of these attack methods, the victim is sent an email in an attempt to trick them into trusting the sender and either revealing sensitive information or transferring funds. Typically, the attacker does enough research to know the name and email address of their target, and the person in the company who would normally ask for large sums of money to be wired somewhere. We’ll call this person the requester. Often the target is the CFO and the requester is the CEO.
In practice, the BEC attack is fairly simple. The attacker sends an email that appears to be from the requestor, to the target. This email requests that a wire transfer be made to a specific account. If the attacker sends a well-crafted email and asks for an amount of money that doesn’t raise suspicion, they will likely reap the rewards of this scam. Blow is a sample BEC email.
These types of attacks have been happening for more than 10 years, but many people have never heard of them. As targets have become more savvy at identifying phishing attacks, the attackers have changed their approach.
How to Protect Against BEC
With a few small changes to your business processes, you can greatly reduce the risk of being a victim of a successful BEC attack.
Education and Awareness: The most important thing you can do is to be aware of this type of attack. Understand that this happens a lot in the business world and make sure that your team knows how to identify these types of scams. I have written about advanced phishing attacks in the past but your company needs regular education and awareness training, even if you are a small company--maybe especially if you are a small company.
Test Your Employees: If your company does not have a cybersecurity education and awareness program that includes internal phishing tests of your employees, consider starting that project. The results are typically eye-opening, but studies show that regular testing of employees makes them much better at identifying phishing attacks.
Verification Processes: Then, institute processes around money transfers that require secondary verification using a different communications medium. For example, if a request comes in through email, verify with the requester over a phone call.
Hire an Expert: Even small and medium sized businesses are being targeted with BEC attacks. While the large corporation likely has a staff of cybersecurity experts on hand who mitigate attacks and manage an education and awareness program, small businesses likely do not. So find an expert. Here are a few companies to review to get you started on you search. And here is a CSO magazine review of some of the top companies in this business.
Remember that your email inbox is a dangerous place! Anyone in the world can send you an email. I’m sure you have a spam filter but the spammers and phishers who are good at their job, also have those tools, and they work hard to make sure their email gets past the filters. Read all email with the thought in the back of your mind that this might not be what it appears.
How to Protect Against Phishing Attacks
While it is increasingly difficult to identify a well-crafted phishing email, there are some steps that can be taken to reduce the risk of falling victim to a phishing attack.
Look at the email headers. Check the From and To fields for anything suspicious. While we already stated that these can be spoofed, they can be a good first indicator of a suspicious email. Here is how to check the full email headers in Gmail. https://support.google.com/mail/answer/29436?hl=en
Hover over links and be sure to read the url from the first forward slash, back to the left, to see where that link is actually going. For example, http://www.google.com.search.us/query.html is actually going to a server called search.us, not google.com. Again, hovering over a link doesn’t necessarily tell you where it’s going but usually it will give you an accurate link.
Don’t trust short URL’s. Short URL’s are very popular with Twitter and other social media. If you encounter a short URL, verify the destination with a tool or website that will reveal the destination address, like checkshorturl.com.
Stay alert! Don’t leave your guard down when you see something that looks credible, like a reCAPTCHA.
Use a password manager and have it automatically fill in your username and password. If you’re on a phishing site, it won’t paste your credentials into an unrecognized domain. (e.g. microsoft.com vs miicrosoft.com)
Use custom email addresses. If you have a Gmail account, use this trick when registering on a website. If you’re registering on facebook.com, and your email address is [email protected], give Facebook the following email address, [email protected] you will get all email sent to that address but if you ever get unsolicited email sent to that address, you know that it was obtained through Facebook.
Share this information with friends, family and colleagues because knowledge is power.